UPDATE: In a statement late Friday evening, Kaseya CEO Fred Voccola confirmed that the company's Incident Response team caught wind of the attack mid-day and immediately shut down their SaaS servers as a precautionary measure, despite not having received any reports of compromise from any SaaS or hosted customers.
"[We] immediately notified our on-premises customers via email, in-product notices, and phone to shut down their VSA servers to prevent them from being compromised. We then followed our established incident response process to determine the scope of the incident and the extent that our customers were affected," Voccola said.
"We engaged our internal incident response team and leading industry experts in forensic investigations to help us determine the root cause of the issue. We notified law enforcement and government cybersecurity agencies, including the FBI and CISA. While our early indicators suggested that only a very small number of on-premises customers were affected, we took a conservative approach in shutting down the SaaS servers to ensure we protected our more than 36,000 customers to the best of our ability."
So far, the company said they believe their SaaS customers "were never at-risk" and expects to restore service to them in the next 24 hours once it is confirmed to be safe.
According to Voccola, about 40 customers worldwide were affected and the company is preparing a patch to mitigate the vulnerability for any on-premises victims.
"We've heard from the vast majority of our customers that they experienced no issues at all, and I am grateful to our internal teams, outside experts, and industry partners who worked alongside of us to quickly bring this to a successful outcome," Voccola added.
Comment sections on Reddit are now inundated with responses from customers trying to respond to the attack and restore systems.
PREVIOUSLY: Kaseya has announced that it is dealing with a massive ransomware attack that now may be affecting at least eight MSPs and hundreds of organizations.
In a message posted to its website, the remote management solutions provider said it is "experiencing a potential attack against the VSA that has been limited to a small number of on-premise customers only as of 2:00 PM EDT today."
"We are in the process of investigating the root cause of the incident with an abundance of caution but we recommend that you IMMEDIATELY shutdown your VSA server until you receive further notice from us," the company said.
"It's critical that you do this immediately, because one of the first things the attacker does is shut off administrative access to the VSA."
Kaseya has taken down all SaaS instances of its VSA remote monitoring and management tool in light of the attack.
John Hammond, senior security researcher at Huntress, told ZDNet that they were first notified of the attack at 12:35 ET and said it "has been an all-hands-on-deck evolution to respond and make the community aware."
Hammond attributed the attack to the prolific REvil/Sodinikibi ransomware group and Bleeping Computer, The Record and NBC News all also reported that REvil or an affiliate was the culprit. Through an update to VSA software, REvil is allegedly spreading the ransomware widely.
"We cannot emphasize enough that we do not know how this is infiltrated in Kaseya's VSA. At the moment, no one does. We are aware of four MSPs where all of the clients are affected -- 3 in the US and one abroad. MSPs with over thousands of endpoints are being hit," Hammond said before Huntress updated its total to 8.
"We have seen that when an MSP is compromised, we've seen proof that it has spread through the VSA into all the MSP's customers. Kaseya's VSA could be either on prem or cloud hosted. They currently have all of their cloud servers offline for emergency maintenance."
Hammond added that three of Huntress' partners have been impacted, with "roughly 200 businesses encrypted."
He explained that agent.crt is dropped by the Kaseya VSA and is then decoded with certutil to carve out agent.exe, and inside agent.exe it has embedded `MsMpEng.exe` and `mpsvc.dll`.
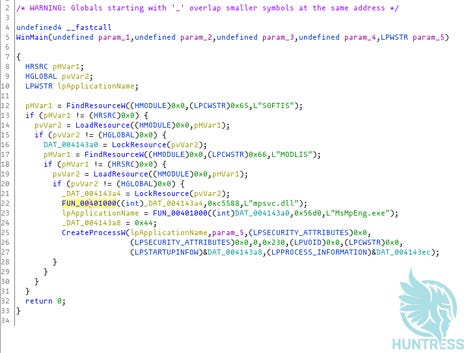
"The legitimate Windows Defender executable was used to side-load a malicious DLL. It is the same exact binary for all victims," he said.
Huntress has a Reddit threat of updates about the situation and said there are indications that VSA admin user accounts are disabled only moments before ransomware is deployed.
CISA released a statement on Twitter that said the organization is "taking action to understand and address the supply-chain ransomware attack against Kaseya VSA and the multiple MSPs that employ VSA software."
Mark Loman, a malware analyst for Sophos, shared a lengthy thread on Twitter about the attack and said some victims are already seeing a ransom page demanding $44,999. Hammond told ZDNet that Huntress has seen ransom demands of $5 million already.
This is far from the first time Kaseya's tools have been used to spread a ransomware attack. As ZDNet has previously reported, REvil's predecessor Gandcrab leveraged Kaseya twice in 2019 to launch attacks, first using a Kaseya plugin then VSA products later that year.
Ransomware actors typically launch attacks on weekends or at night because there are less people watching systems.
Sophos released a detailed guide for potential victims to figure out if they are under attack.
Chris Grove, technology evangelist with Nozomi Networks, said these types of supply chain attacks, like SolarWinds, go "straight to the jugular of organizations looking to recover from a breach."
"These types of technology management solutions can have high concentrations of risk due to their large collection of enterprise accounts with elevated privileges, unrestricted firewall rules needed for them to operate, and a cultural 'trust' that the traffic to/from them is legitimate and should be allowed," Grove said.
"Shut" - Google News
July 03, 2021 at 05:33AM
https://ift.tt/3jCX90p
Kaseya urges customers to immediately shut down VSA servers after ransomware attack - ZDNet
"Shut" - Google News
https://ift.tt/3d35Me0
https://ift.tt/2WkO13c
Bagikan Berita Ini














Lagi ngerasa hoki?
ReplyDeleteayo coba mainkan kartu mu disini Aj0qq*com
Sedia deposit pulsa juga (min 20rb)